First Malicious Driver
How I Created My First Malicious Driver
Disclaimer: This article is for educational purposes only. Writing or deploying malicious drivers is illegal and unethical unless done in a controlled environment for research and learning. Always follow legal and ethical guidelines.
Setting Up the Environment
To create my first malicious driver, I utilized the resources provided by Microsoft’s official documentation on downloading and setting up the Windows Driver Kit (WDK). Here's the step-by-step process I followed:
i followed along with this video to guide me on how to create this project
- Download and Install Visual Studio 2022
- I installed Visual Studio 2022 using the official guide.
- During the installation process, I ensured to select the “Desktop development with C++” workload and added the necessary individual components for driver development, including:
- MSVC v143 - VS 2022 C++ ARM64/ARM64EC Spectre-mitigated libs (Latest)
- C++ ATL for latest v143 build tools with Spectre Mitigations (ARM64/ARM64EC)
- Windows Driver Kit (added later via modifying the Visual Studio Installer).
- Install the Windows SDK
- Using the provided link, I downloaded and installed the Windows SDK version
10.0.26100.2454to ensure compatibility with the driver kit. This is essential as mismatched versions between the WDK and SDK can lead to build errors.
- Using the provided link, I downloaded and installed the Windows SDK version
- Install the Windows Driver Kit (WDK)
- After installing the SDK, I downloaded and installed the Windows WDK of the same version (
10.0.26100.2454). The WDK integrates seamlessly with Visual Studio for driver development.
- After installing the SDK, I downloaded and installed the Windows WDK of the same version (
Writing the Driver Code
Once my environment was set up, I wrote a simple kernel-mode driver. The driver was designed to print a debug statement that said, “My first Malicious Driver.” Below is a simplified outline of the code I used:
#define _AMD64_
#include <wdm.h>
NTSTATUS DriverEntry(void* a, void* b) {
DbgPrint("My first Malicious Driver");
return STATUS_SUCCESS;
}
Key points in the code:
- DriverEntry: This is the entry point of the driver and is executed when the driver is loaded.
- DbgPrint: This function outputs debug messages to the kernel debugger.
cl driver.c "C:\Program Files (x86)\Windows Kits\10\Lib\10.0.22621.0\km\x64\NtosKrnl.lib" /I "C:\Program Files (x86)\Windows Kits\10\Include\10.0.22621.0\km" /link /subsystem:native /driver:wdm -entry:DriverEntry
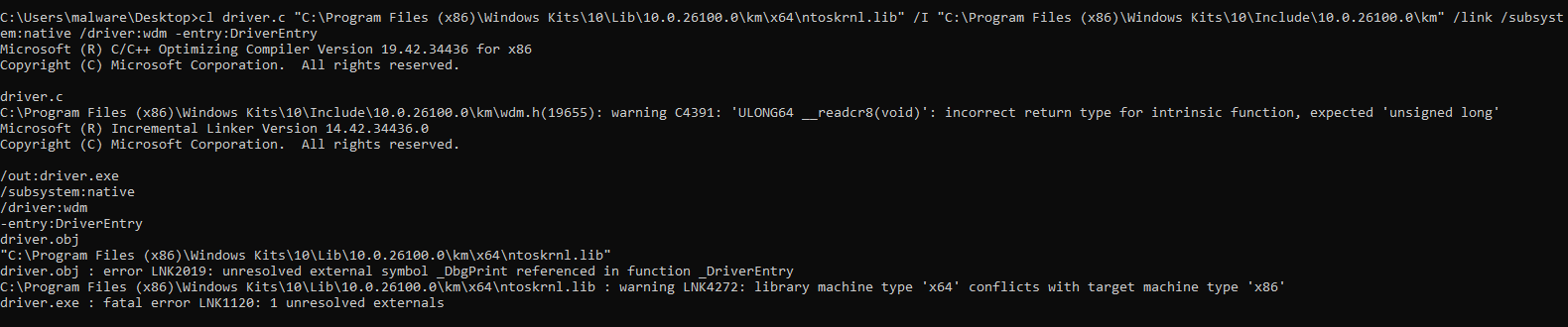
Building and Compiling the Driver
- Set up the project in Visual Studio:
- Created a new project for a “Windows Kernel Mode Driver (KMDF).”
- Included the necessary libraries and headers provided by the WDK.
- Build Configuration:
- Set the build configuration to “Release” for
x64architecture. - Built the driver, which produced a
.sysfile as the output.
- Set the build configuration to “Release” for
ren driver.exe driver.sys
Testing the Driver
- Set up a Virtual Machine:
- To avoid affecting my host system, I tested the driver in a controlled virtual machine environment.
- Enable Unsigned Driver Mode:
- To allow unsigned drivers to run, I restarted the VM and enabled the option by following these steps:
- Hold Shift and click "Restart" to access advanced startup options.
- Navigate to "Startup Settings" and press
7to disable driver signature enforcement.
- To allow unsigned drivers to run, I restarted the VM and enabled the option by following these steps:
- View Debug Output:
- Downloaded and used DebugView to capture and view the output of the driver.
- Confirmed that the debug message "My first Malicious Driver" was successfully displayed in DebugView.
Used the sc command to create and start the driver service:
sc create infinit3iDriver binPath= C:\Users\Nir\poc\driver\driver.sys type= kernel
sc start infinit3iDriver
Conclusion
Creating this driver was a fascinating learning experience. It provided insights into how kernel-mode drivers interact with the operating system and how they can be abused if misused. Again, I emphasize the importance of using such knowledge responsibly and legally.